Unknowndevice64–1: Vulnhub Walkthrough

Hello Guys! This is Russell Murad working as a Junior Security Engineer at Enterprise Infosec Consultants (EIC).
In this writeup, we’ll break a machine named “Unknowndevice64:1”.
It’s been said in the description that it’s an intermediate level box.
But I personally felt it’s an easier one.
So, let’s get started…
- First, we use “arp-scan -l” for enumerating target IP.

2. We’ll use Nmap for finding some open ports. You’ll see there are two open ports. One is SSH, another one is HTTP.

3. We can try nikto for server vulnerability scan but nothing important there.

4. Now we’ll check the HTTP part. Let’s open up the IP with firefox.

5. Nothing interesting there. So, let’s check the source file.
We’ll find a commented out string there.

6. It might a directory. So, we’ll try it out with the browser.
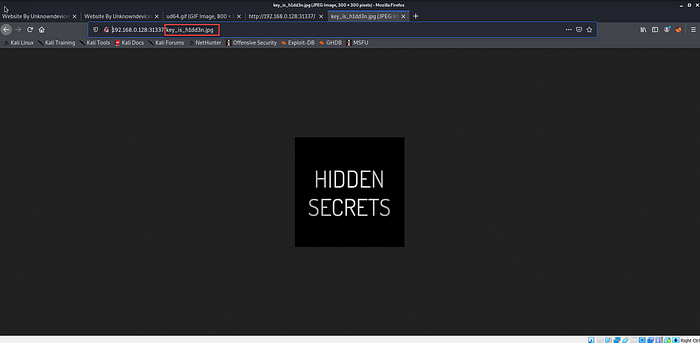
And there it is! It’s an image sealed “Hidden Secrets”. At this point, We're confident that there might be some secret hidden inside it.
Let’s download the image now.
7. We’ll open it using steghide, use “h1dd3n” as a passphrase.
We’ll see some hidden message encrypted with Brain Fuck.

8. Using this site, we’ll decrypt the message.
Observe it, it’s a string with username: password formate.
Let’s try it out with SSH.

9. Using that username, password we’ll successfully be logged in.
But the problem is now, it’s a rbash restricted shell environment.
Very few commands can run here now.

10. For more details we can run man command.

11. We found some tricks online, you can read one of them from here.
In short, in this environment, we can use vi aka vim.
With vi, we can run Linux commands. What if we run a command which will call bash instead of rbash and with this bash we can run other commands also.
Let’s try.

First, we’ll type “vi”, then in the vi, we’ll put these commands for the bash.
12. Now, we’ll export the shell, path variable for the bash.
We can see everything is working smoothly now !

13. Let’s check file permission using “sudo -l”. We’ll find out that the program sysud64 can run without using the root password.

Again there’s a problem. sysud64 won’t work properly here.
Let’s check “sysud64 -h” for details.
14. It’s the strace file, sysud64 is an alias for this file.

15. We’ll search in gtfobins for checking if something useful and there it is.

16. Let’s use this payload with some replacement.

17. We’ve gained root privilege, let’s check out our desired flag file.

So, guys, that’s it for today.
Thank you for reading this write-up. Cheers!