Stapler-1: Vulnhub Walkthrough

Hello Guys! This is Russell Murad working as a Junior Security Engineer at Enterprise Infosec Consultants (EIC).
In this writeup, we’ll break a machine named “Stapler-1”.
If you check the description, it says in there,

“At least two (2) paths to get a limited shell”
“At least three (3) ways to get a root access”
So, yeah, there are many approaches for solving this box.
You can download this machine from here.
So, let’s get started…
- As usual, We’ll find our victim machine using arp-scan.

2. Now, we’ll use Nmap for port scanning.


3. We’ve found some open ports. HTTP service runs on this server — 80,12380.
Now time to directory brute-forcing. Nothing interesting here.

4. We’ll use Nikto for the vulnerability scans. Same here. Nothing important.

5. Now let’s try to login in FTP server. We’ll use “anonymous” as a username, password. There’s a note which we’ll download.

6. After opening it, there is a message.

Nothing important except we’d found two usernames — Elly, John.
7. Now, we’ll create a text file named user.txt, put those two names into that file, and try to brute force the FTP server for passwords using hydra.
We’ll found a password successfully for the username — elly.

8. We’ve tried to log in with the password but no luck.
9. Now let’s open their website using 12380 port.

10. Here’s the thing, if we use HTTPS instead of using HTTP we’ll found something interesting.

11. We’ll do directory bruteforcing using ffuf.

12. Let’s browse the robots.txt file.

13. We’ve got two pages — admin112233, blogblog, etc. Which we’ll browse one by one.
While we browser — admin112233 there’s a pop-up. Nothing important.
14. Now, let's check “/blogblog”. We can assume it as a WordPress file.

15. We’ll use “Wpscan” for WordPress enumeration. Keep in mind that we’ve to add an additional parameter “disable-tls-checks”. Otherwise, there’ll be an error.



16. We’ll Bruteforce password for those usernames, end up only for four passwords.

17. For more enumeration let’s check out the plugins section of that blog. There’s a plugin named “advanced-video”.

18. We’ll search in google for some information about this plugin and found an exploit in exploitdb.


19. As per its instruction, we’ll browse that link, put some garbage value in the “thumb” parameter.

20. There's a link! Which we’ll use for getting the wp-config.php file.

21. Here we’ll get another link.

22. Let’s check it on the browser. We’ve to change “=” into “-” for browsing. We’ll found there’s an image.

23. If we check the “/upload” folder now. The image will be there.

24. We’ll download the photo and open it. We’ll see that the photo contains the whole “wp-config.php” file.


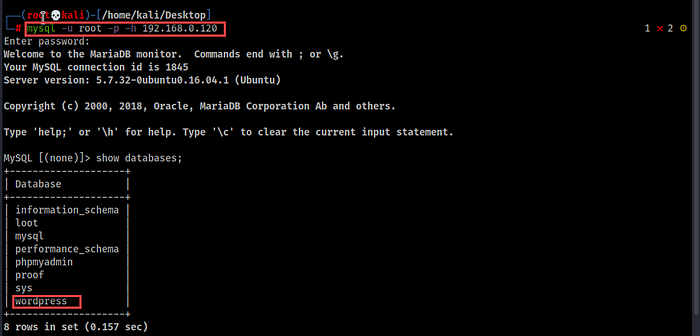
25. Now we’ll log in to the database of this site using the root username, password.
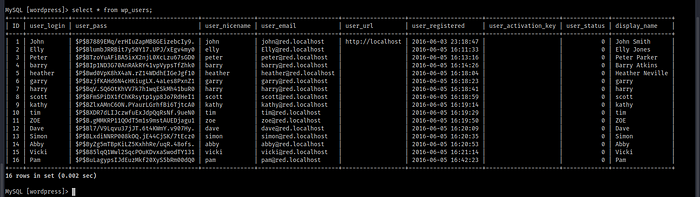
Then, in the wp_users table, we’ll found that the whole username, passwords are stored there!

26. Now we’ll fire up Hashcat for cracking those hash we’ve found.
We can assume john is the admin. We’ll use the password to leverage it.

27. Let’s login into WordPress using john’s username, password.

28. Now we’ll go to Plugins and upload pentest monkey’s reverse-php-shell.

29. We’ll open up NC and will get a response from the server.


30. The server is Ubuntu 16.04 LTS version. If we check exploitdb we’ll found an exploit for this server. Here’s the link.
31. As the exploit said, we’ll download it and unzip it properly.

32. Now we’ll go to “/ebpf_mapfd_doubleput_exploit”. Run the “./compile.sh”.
After that run the “./doubleput”.
And we’ve finally able to get our root privilege.
Easy right?

33. Finally, we’ll head straight for the /root folder.
open up the flag file.

So, guys, that’s it for today.
Thank you for reading this write-up. Cheers!