SICKOS:1.1 Vulnhub Walkthrough
Hello everyone. This is Russell Murad working as a Junior Security Engineer at Enterprise Infosec Consultants (EIC).
Today, we’ll see how to solve “SickOS:1.1” from vulnhub.
As we can see in the description section of the vulnhub site, it says, “This vm is very similar to labs I faced in OSCP.”. So, It’s an OSCP style box from which you’ll be benefited if you’re preparing for OSCP and especially you’re a newbie like me… :P
So, let’s begin…
I’ve configured both Vulnhub machine and my kali machine on the Virtualbox bridge connection.
- First, we are going to check our victim machine’s IP using arp-scan.

2. Then we need to find some open ports using nmap.

3. Here we’ve found two-port — 22 for SSH and 3128 for Squid http-proxy.
From Wikipedia, we can know that 3128 port is used for caching and Forwarding HTTP web proxy. Now we’ll fire up nikto — using it’s “useproxy” command.

4. From the result we are pretty sure that the server has Shell Shock Vulnerability. Now we’ll set up that proxy in the browser and try to access the website using the port.


It’s working !!!
5. Now we can browse the site properly and try to figure out if there any “robots.txt” file and guess, it’s there! We found there a directory called “wolfcms”.

6. We’ll browse that directory and discovered that it’s CMS called wolfcms.

7. Now we’ll go to exploitDB and search for it. There is a working exploit that leverages file arbitrary file upload.

8. We’ll follow those and login into the admin panel.

9. we’ll try first using admin as the username, password. It’ll work!

10. There’s a “files” section and in that section, there is an “upload file” function. We’ll upload the pentest monkey’s PHP reverse shell. At the same time, we’ll open an nc in our kali command line.

11. Now we’ll run “…/public/Shell.php ” in the browser and get the response from the reverse shell.


12. From there we’ll import python spawn bash and goto “/var/www/wolfcms”. Then open the “config.php” file using cat command.

13. There is a lot of juicy information about the DB, containing dbname, user, pass. We’ll use this information to login to the SSH port.
First, we tried various usernames like root, john — nothing will work.
But when we’ll use “sickos” as the username, it’ll work —

14. We’ll run “sudo -l” to know which commands this user can run.
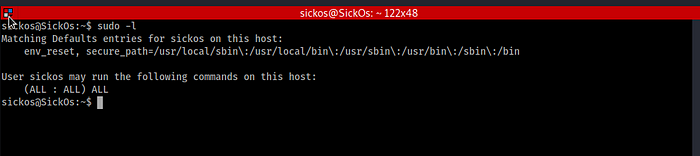
We’ll see that this user can run every command.
15. Now we’ll go for “sudo su -”, gain root access and open our desired flag file.

So, guys, that’s it for today! Hope we’ll see in the next write-up.
Thank you for reading this write-up. Cheers!