Pluck-1: Vulnhub Walkthrough

Hello Guys! This is Russell Murad working as a Junior Security Engineer at Enterprise Infosec Consultants (EIC).
In this writeup, we’ll break a machine named “Pluck:1”.
You can download it from here.
I’ve configured both Vulnhub machine and my kali machine on the Virtualbox bridge connection.
- First, we are going to check my victim machine’s IP using arp-scan.

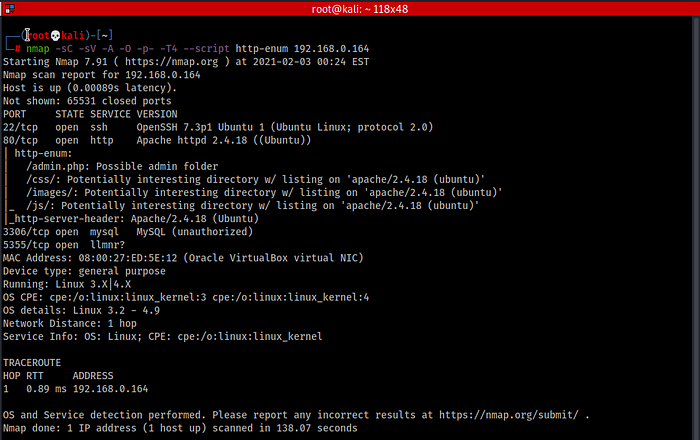
2. Then let’s try to find out some open ports using Nmap.
3. We’ll use GoBuster for Directory Brutforcing.We’ll get some files but while checking in the browser, unfortunately, none of them seems interesting to me.

4. Now we’ll try nikto. At that moment, you’ll see that the file “index.php” has a path traversal vulnerability. Let’s leverage it.

5. We’ll open up the affected link into the browser and here you can see, it says that “Just to make backups easier” and also the path is there.

16. Again using the given path, we modify the link, hit it into the browser and there’s another message. Which says, “we can get it via tfpt”.

17. Let’s go to the command line and access the backup using tftp.

18. After the download, extracting the tar file and accessing folders we’ll discover in paul’s directory, there is a lot of RSA key which we could use for leveraging SSH port.

19. We’ll try them one by one for login into paul’s account with SSH where id_key4 will work!

20. After login, there will a box open like this.

21. We’ll try with every option for discovering something important.
While we’re checking the “Edit file” option, we’ll see it’ll open up a VI editor.
We know that the VI editor can run Linux commands.
Let’s use this to open up a shell for us. We’ll set the PATH for a shell like this:

22. Open up the shell.

23. Damn, an interactive bash shell is here.

24. Now it’s time to privilege escalation. We’ll search for some SUID privileged binary files.
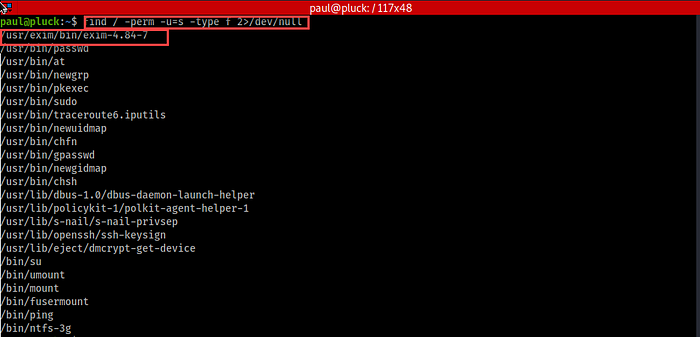
Here… We have a file name “Exim” which is different than others.
25. Let’s use the searchsploit now, whether any kind of exploit for that.
We’ve got it. There’s a Local Privilege Escalation exploit which we’ll use.

26. Let’s go to the “/tmp” directory and copy-paste it using VI editor, save it by naming “exploit.sh”.

27. We’ll run it now and gain our root access! Sweat! Isn’t it?
Let’s go to the root folder and cat the flag.txt file.

So, guys, that’s it for today.
Thank you for reading this write-up. Cheers!