JIS-CTF: Vulnhub Walkthrough

Hello Guys! This is Russell Murad working as a Junior Security Engineer at Enterprise Infosec Consultants (EIC).
In this writeup, we’ll break a machine named “JIS-CTF”.
If you check the description, it says in there, “There are five flags on this machine. Try to find them. It takes 1.5 hours on average to find all flags.”

That’s true I never found such easy vulnerable machine till now.
Anyway, You can download the machine from here.
Now, let’s get started…
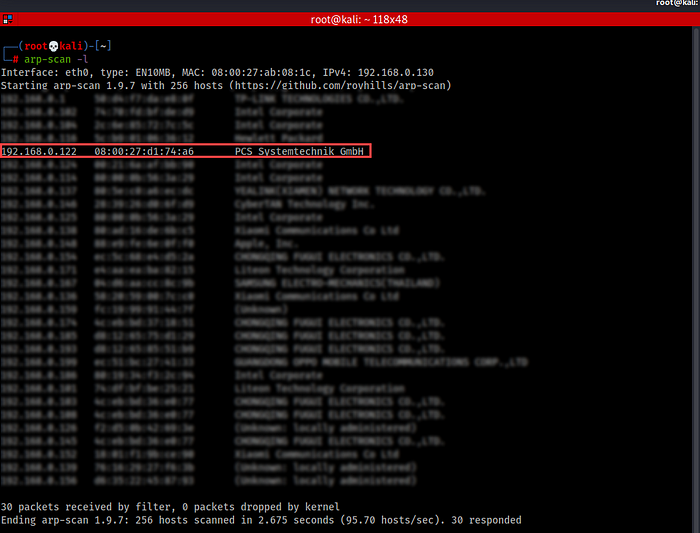
- Just like every time, We’ll find our victim machine using arp-scan.
2. Now, we’ll use Nmap to discover open ports.

3. Now we’ll use goBuster for finding some directory.

4. Let’s check out the “robots.txt” file. There are some directories…
We’ll check those out one by one.

5. Surprisingly, we’ll find out our first flag just by visiting the directory “flag”.

6. Now if we visit the directory “admin_area” we’ll see this message, “The admin area not work”. But if we check the source code, we’ll find out the second flag and a username, password.


7. Let’s use this id, password for logging in “login.php”.


It’ll work. We are successfully logged in right now. We can see, here, and upload file feature that we can leverage for reverse shell upload.
8. We’ll open up a Netcat listener and upload the reverse shell from the pentest monkey. But here’s the thing for some time being I couldn’t understand where the file was gone!
After some analysis, I discovered the directory from the “robots.txt” file. There’s a directory named, “uploaded_file”. From which we can access our uploaded shell file.
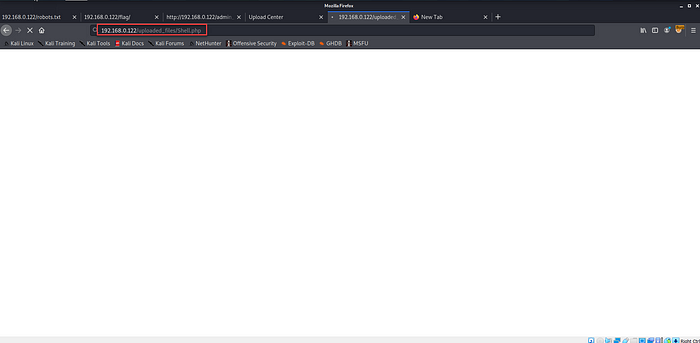
If we browse the directory, our nc will get a response from the server.
9. Now, We’ll find out our third flag from “/var/www/html” folder. The file name is hint.txt.

10. Finding the fourth flag will take some time. After 10 minutes we’ll discover the file “Credential.txt” from “/etc/mysql/conf.d” folder.

There are another username and password we’ll get in there.
11. We’ll use that username, password to login SSH. And find the final flag in a file name flag.txt from “/var/www/html” folder.
This is a really basic stuff. Doesn’t face any sort of trouble while solving it.
So, guys, that’s it for today.
Thank you for reading this write-up. Cheers!