Hackme-1: Vulnhub Walkthrough

Hello Guys! This is Russell Murad working as a Junior Security Engineer at Enterprise Infosec Consultants (EIC).
In this writeup, we’ll break a machine named “Hackme:1”.
Vulnhub said it’s a beginner level box, so do I.
You can download it from here.
I’ve configured both Vulnhub machine and my kali machine on the VMware NAT connection.
- First, we are going to check our victim machine’s IP using arp-scan.

2. Then let’s try to find out some open ports using Nmap. Only two ports open here! No problem.

3. We’ll use GoBuster for Directory Brutforcing. Here’s some directory we’ve found —

4. Let’s check “login.php” in our firefox browser -

5. Let’s create an account. We’ll discover a search option let’s check on that for possible SQLi vulnerability.



And guess what! It’s vulnerable to SQLi!
6. Let’s identify the total number of columns -


7. We’ll search for DB name is being used here()-


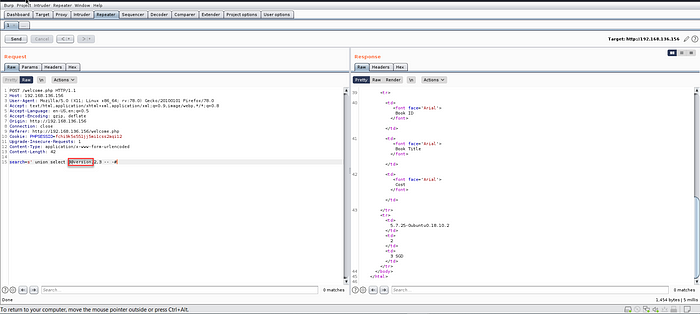
8. Now, Identifying the DB version -

9. Now let’s list all DB from the backend —


10. Let’s extract all tables name-


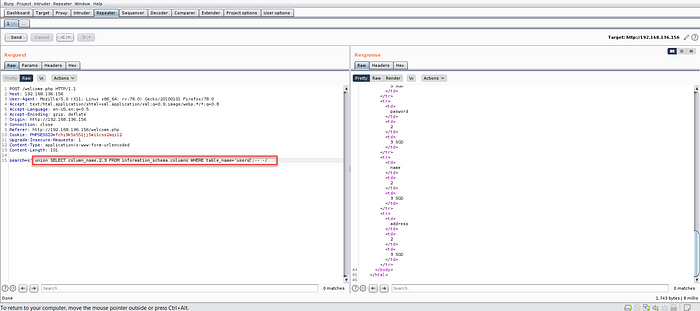
11. We’ll extract all column names one by one from every table now.



12. Let’s dump all the information from the table, “user, password”-


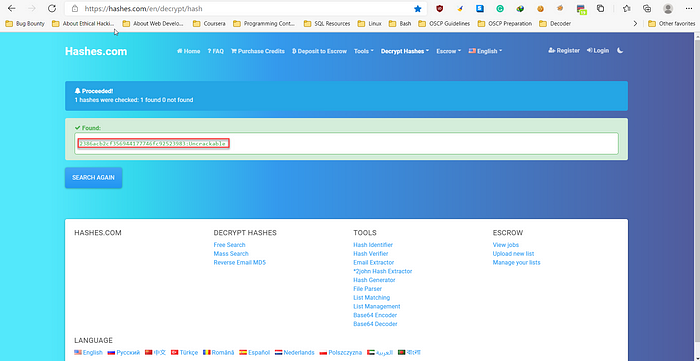
Here we’ve found an encrypted password for super admin.
13.Let’s crack it from online. We’ll use hashes.com.
14. Let’s log out from our account. Try to login with our new “superadmin” user password.

Success! Look at the upload image option. Let’s try to upload a shell without modifying it, we’ll check for a bypass next if it’ll not work.
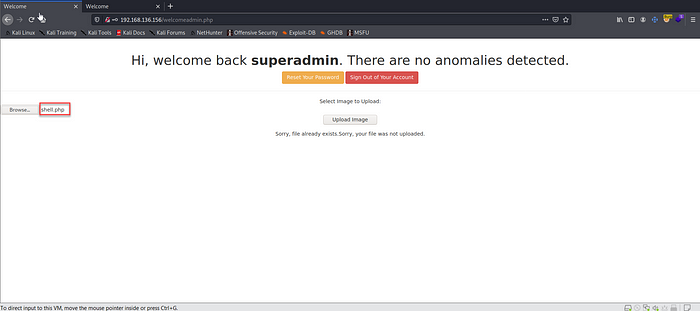
15. But there’s no need for it. If we check the upload folder we’ll see it has been successfully uploaded.

16. Now open up an NC and we’ll see that NC got a response from the server.

17. Now we’ll search for good SUID permitted binary files.

18. Here it is! Do you feel something unusual about it! Its directory is different than every other file. We’ll run it! and guess what we’ll get a root. Too much easy! Isn’t it?

So, guys, that’s it for today.
Thank you for reading this write-up. Cheers!