Hackacademic.RTB-1: Vulnhub Solution
Hello Guys! It’s me, Russell Murad, working as a Junior Security Engineer at Enterprise Infosec Consultants (EIC).
In this writeup, we’ll solve a vulnerable box called “Hackacademic.RTB-1”.

It’s a beginner-level box.
You can download it from here.
I’ve configured both the Vulnhub machine and my kali machine on the VMWare Workstation NAT connection.
So, let’s begin –
- First, we’ll use arp-scan to check our victim machine’s IP address. Command –
arp-scan -l
2. After that we need to find some open port and service enumeration. So, we’ll use Nmap for that. Command –
nmap -sC -sV -A -O -p- -T4 --script http-enum 192.168.136.157
Here, we can see that we’ve got only one open port — 80, which is HTTP.
3. Now enumerating server vulnerability, we’ll use Nikto.
nikto -h 192.1nikto -h 192.168.136.15768.136.157
4. Now let’s use wpscan for enumerating the WordPress site.
wpscan --url http://192.168.0.153 --api-token <token>

wpscan has detected 16 vulnerabilities so far!
One of them is SQL Injection.
Let’s exploit this vulnerability manually.
5. We’ll go to the site and check the vulnerable parameter. In this case, it is “cat=1”.

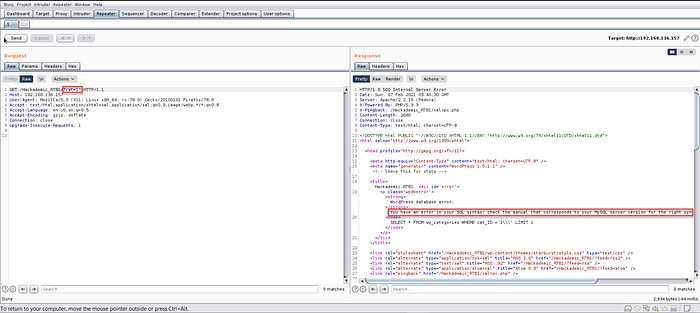
6. For making the work easier, we’ll fire up the burp and send the request to the repeater. When we put a single quote (‘) to the request, it’ll show the error message into the request.
7. Now, we’ll use “order by” clause to find out column numbers.

8. After that, we’ll retrieve the table’s information.

9. Here, we can find out the database version, username if we like.


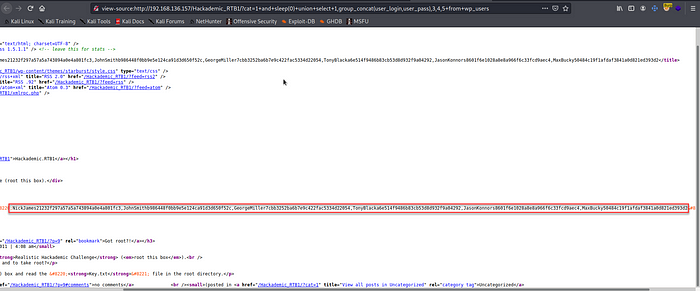
10. Now we’ll retrieve user_id, user_pass from the wp_user table.

11. Let’s decrypt those encrypted passwords from the website called “hashes.com”.
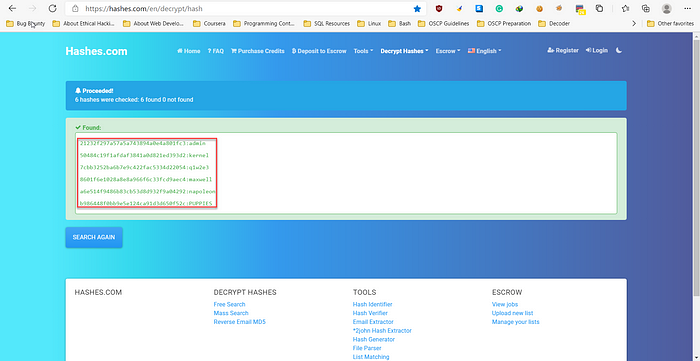
12. We’ve found those password for each respected users–
NickJames:adminJohnSmith:kernelGeorgeMiller:q1w2e3TonyBlack:maxwellJasonKonnor:napoleonMaxBucky:PUPPIES
13. Only two of those will work. Except for those two, every user : pass combination will produce either username error or password error.
14. Now, if we log in with user GeorgeMiller, then we’ll find out the file section. Let’s place there our reverse shell.


15. If we open up netcat with port 4444, then we’ll find a response.

16. After getting a shell, I’ve searched for exploit online, most of them didn’t work. But here is an exploit found in security focus that will work for our version.


17. Let’s compile with gcc and run it. Command –
gcc RDS.c -o exploit

And here you can see, we’ve just gained our root privilege and find the key.txt file!!!
So, guys, that’s it for today.
Thank you for reading this writeup. Cheers!