DerpNStink-1: Vulnhub Walkthrough
Hello Guys! It’s me, Russell Murad, working as a Junior Security Engineer at Enterprise Infosec Consultants (EIC).
In this writeup, we’ll solve a vulnerable box called “DerpNStink-1”.
You can download the machine from here.

If you go to their official site, it says, it’s a beginner level machine. I personally find it like medium level difficulty.
It says, “Your goal is to remotely attack the VM and find all 4 flags eventually leading you to full root access.”
I’ve configured both the Vulnhub machine and my kali machine on the virtual box bridge connection.
So, let’s begin –
1. First, we’ll use arp-scan to check our victim machine’s IP address. Command –
arp-scan -l
2. After that we need to find some open port and service enumeration. So, we’ll use Nmap for that. Command –
nmap -sC -sV -A -O -p- -T4 — script http-enum 192.168.136.157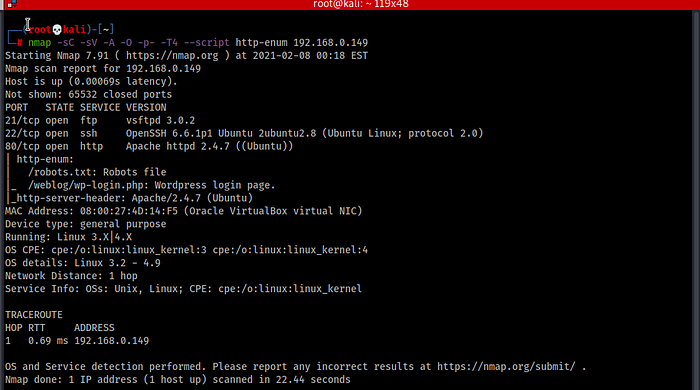
Here, we can see that we’ve got three open ports — 21,22,80 which is FTP, SSH, HTTP.
3. Now, we’ll use a directory bruteforcing tool called “goBuster” for finding some directory and files. Command –
gobuster dir -u http://192.168.0.149/ -x php,txt,bak,old,zip,gz,conf,cnf,js -w /home/kali/Desktop/Big.txt -t 40
4. Let’s browse the site now. After opening up the URL to the browser, while we’re checking the source file, we’ve found our first flag! Three to go!
←flag1(52E37291AEDF6A46D7D0BB8A6312F4F9F1AA4975C248C3F0E008CBA09D6E9166) →
5. If we try to load our “/weblog” directory, we’ll see that it’s won’t load properly.
So, we need to add our target URL to the “/etc/hosts” file. Let’s add it-

6. Now run it into firefox again.

It’s a WordPress site! Time to fire up wpscan!
7. We’ll use wpscan for enumerating username. Command –
wpscan — url http://derpnstink.local/weblog/ -e u

We’ve got two username — admin, unclestinky.
8. In pentesting scenario, we often find users careless and they sometimes use their username and password the same. For the case of this box is the same. We’ll use password, “admin” like the username, and guess what it’ll work!


But after traveling to the site, we’ll understand it’s not the admin account as we thought.
It has lower level privilege.
But still, there is a Slideshare section on which we can upload images. We’ll try to upload a reverse shell here.
In the previous enumeration wpscaner also said the same that there a file upload vulnerability.


9. We’ll add a Netcat listener and get the response. Command –
nc -nlvp 4444
10. Let’s travel into the “/var/www/html” section little bit. We’ll search for the “wp-config.php” file.
After some moments we’ll find it to the “/var/www/html/weblog” directory.
Let’s read it. Here we’ve got the DB user, password — root:mysql

11. We’ll use those credential to log in to the MySQL database of this server -

12. In wp_users table, there’s our two user’s password. One is already we know — admin.
Another one is in an encrypted format which we don’t know yet.

13. Let’s use hashcat to crack that password –


After almost half an hour, it’ll crack, and the password is — wedgie57.
14. Now, let’s use the username, password and log in to SSH.

Here, you can see it says that “permission denied”.
15. Now, we’ll try to same with the FTP port. Fortunately, we’ll get success into it this time.
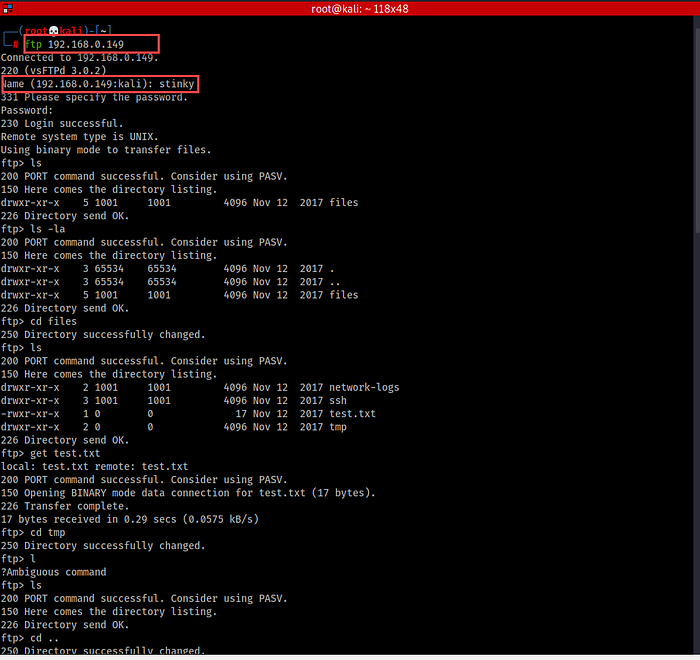
16. After enumerating some time, here is a “key.txt” file we’ve found –
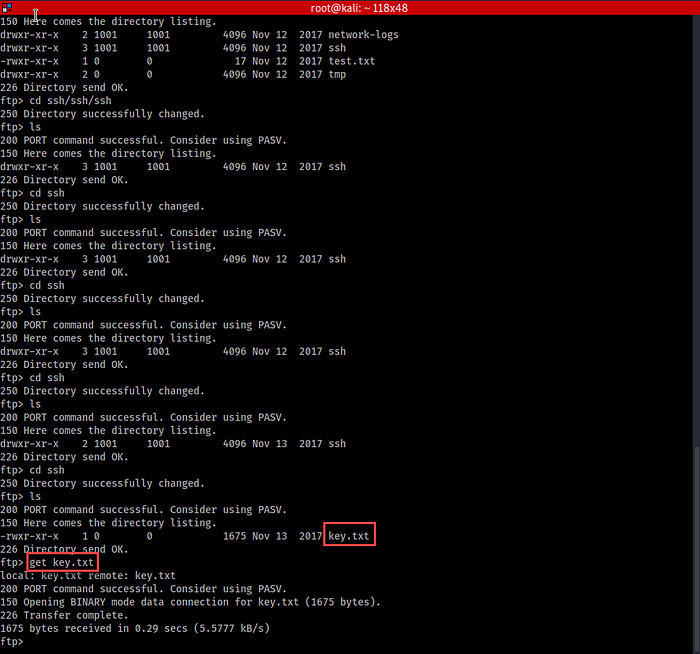

17. Nice! It’s an RSA key. RSA key is used for login SSH. Let’s use it to login SSH again.

Oops! Need to change the permission. Command –
chmod -rwx key.txt
It worked!
18. After enumerating Desktop. We’ll found our third flag –
flag3(07f62b021771d3cf67e2e1faf18769cc5e5c119ad7d4d1847a11e11d6d5a7ecb)
19. After getting all this, we decide to check the WordPress site again. This time with stinky’s credential. At first, we’ve failed to login with the username “stinky”, but when we tried with “unclestinky”, it’ll work.


And look at the dashboard. There we get our second flag –
flag2(a7d355b26bda6bf1196ccffead0b2cf2b81f0a9de5b4876b44407f1dc07e51e6)After that, there’s not so much interesting in that WordPress file.
20. There’s a folder called “network-logs” in SSH. In that folder, we’ll get a text file “derpissues.txt”.
After opening it, we’ll discover about a conversation between “mrderp” and “stinky”.
There are some issues with “mrderp”’s account and stinky is telling him that he’s going to capture some packets to figure it out.

21. There’s a pcap file in the “Documents” folder we’ll discover after some enumeration.

22. 1. Let’s transfer it into our kali machine using scp. Command –
scp -i key.txt stinky@192.168.0.149:/home/stinky/Documents/derpissues.pcap /home/kali/Desktop
23. Let’s open it up using “wireshark” –


24. We’ll use “TCP Stream” for getting a more clear view.


Here’ we can see, “mrderp”s password is — derpderpderpderpderpderpderp .
25. Let’s get back into our SSH. Now, change the user using — su mrderp.
We’ll use the password which we’ve just found.

26. While we’re enumerating into “mrderp” account, we’ll found a log file, named “helpdesk.log”, talking about sudoers file issues in the Desktop directory.


There’s also a Pastebin link given in that file. We’ll open it in our browser.
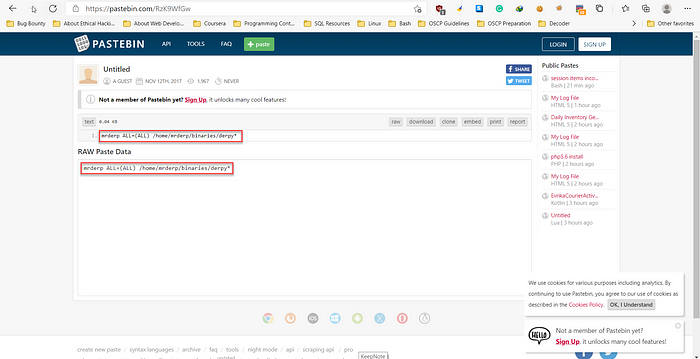
It says that, /home/mrderp/binaries/derpy can run in sudo privilege.
27. There are no “binary” folder in “/home/mrderp” folder. Let’s create those-

28. And we’ll make a derpy file which will be a bash file, where we’ll put a one-liner reverse shell.

29. Now open up a Netcat listener and run that derpy.sh file with sudo privilege.
We’ll see our NC will get a response from the server and also it’ll get the root privilege.
Now cat the flag file and check it, it’s our fourth flag –
flag4(49dca65f362fee401292ed7ada96f96295eab1e589c52e4e66bf4aedda715fdd)
So, guys, that’s it for today.
Thank you for reading this write-up. Cheers!









